Posted by: Dharun VM
Imagine you’re about to unlock your car with your key fob. The car doesn’t just open because something sent a signal — it opens because it recognizes and trusts that the signal came from your key.
That moment of recognition — where one system verifies that another is legitimate — is called authentication.
In the digital world, authentication works the same way.
It’s the process of confirming that a user, device, or system really is who (or what) it claims to be. In simple terms, it answers the question:
“Can I trust this source before I share my data or accept its commands?”
Modern vehicles are no longer isolated machines; they’re complex networks on wheels, filled with dozens of Electronic Control Units (ECUs) constantly talking to each other.
When an ECU sends a message — say, to control the brakes or update the engine firmware — how does the receiving ECU know that message is genuine and not from a malicious device pretending to be part of the car?
That’s where authentication steps in.
It ensures that communication between ECUs (or between a diagnostic tester and an ECU) happens only between trusted parties. Without it, attackers could inject fake messages, manipulate safety-critical functions, or even install unauthorized software.
At its core, authentication is all about proving identity.
In computing, this is usually done in three main ways:
- Something you know – like a password or secret key
- Something you have – like a digital certificate or cryptographic token
- Something you are – like a fingerprint (in humans, less common in ECUs)
In the automotive world, it’s usually the second type — something you have.
ECUs use digital certificates and cryptographic keys to prove who they are. These credentials are part of a larger framework called Public Key Infrastructure (PKI), which helps vehicles establish trust in a secure and verifiable way.
With vehicles now supporting over-the-air (OTA) updates, remote diagnostics, and vehicle-to-everything (V2X) communication, authentication has become more critical than ever.
It’s the first layer of defense in vehicle cybersecurity — ensuring that every connection, every message, and every update comes from a trusted source.
In the modern automotive ecosystem, vehicles are no longer isolated machines — they’re intelligent, connected systems constantly exchanging data with ECUs, sensors, diagnostic tools, and even cloud services.
As connectivity grows, so does the need to ensure that every message, every command, and every piece of data exchanged inside or outside the vehicle is authentic and secure.
This is where authentication becomes a cornerstone of in-vehicle cybersecurity.
UDS Authentication Service (0x29): An Overview
UDS (ISO 14229) defines a range of services for diagnostics and security.
Service 0x29 – Authentication specifically handles secure communication establishment between a client (tester) and an ECU (server).
The authentication process in UDS can follow multiple methods depending on the implementation and security requirements. Two commonly discussed mechanisms are:
- ACR (Authentication with Challenge–Response)
- APCE (Authentication with PKI Certificate Exchange)
Both methods aim to verify the authenticity of the communicating parties — but they differ in how trust is established and maintained.
Understanding ACR (Authentication with Challenge–Response)
The ACR mechanism is the simpler of the two.
Here’s how it works conceptually:
- The client sends an authentication request to the ECU.
- The ECU responds with a challenge — typically a random number or nonce.
- The client uses a shared secret or preconfigured key to compute a response (usually by encrypting or hashing the challenge).
- The ECU verifies this response using the same secret or key.
If the response is valid, the ECU considers the client authenticated.
Advantages of ACR:
- Simple and lightweight implementation
- Suitable for low-complexity ECUs
- Low computational overhead
Limitations of ACR:
- Relies on pre-shared secrets, which must be securely stored in both ECU and tester
- Difficult to manage or rotate keys across a large vehicle fleet
- Limited scalability in connected vehicle architectures
- Vulnerable if the shared key is compromised
As vehicles evolve toward connected ecosystems, these limitations make ACR less ideal for long-term security.
Introducing APCE (Authentication with PKI Certificate Exchange)
To overcome ACR’s limitations, the automotive industry has moved toward APCE — Authentication with PKI (Public Key Infrastructure) Certificate Exchange.
This method provides stronger security, better scalability, and easier key management.
Here’s how APCE typically works:
- The client initiates an authentication request.
- The ECU sends back a challenge along with its certificate (which contains its public key and identity information).
- The client verifies the ECU’s certificate using a trusted Certificate Authority (CA).
- The client then responds with its own certificate and a digital signature over the challenge or other agreed data.
- The ECU verifies the client’s certificate and signature.
- Once mutual authentication is complete, a secure session key can be established for encrypted communication.
Unlike ACR, APCE doesn’t depend on shared secrets.
Instead, it uses asymmetric cryptography — where each entity has its own public and private keys — making the system both secure and scalable.
Understanding the Certificate and Certificate Chain in APCE
When APCE is used, digital certificates become the heart of authentication.
They’re like electronic ID cards for ECUs and diagnostic tools, based on the X.509 standard.
They are usually based on the X.509 standard and contain structured information that allows verification and trust establishment.
A typical X.509 certificate used in APCE includes:
| Field | Purpose |
| Version | Indicates the X.509 format version (usually v3). |
| Serial Number | Unique identifier assigned by the Certificate Authority (CA). |
| Signature Algorithm | The algorithm used to sign the certificate (e.g., ECDSA with SHA-256). |
| Issuer | The CA that issued the certificate. |
| Validity Period | Start and expiry dates for the certificate. |
| Subject | The entity the certificate belongs to (ECU or tester ID). |
| Subject Public Key Info | Contains the public key of the entity and key type (ECC, RSA, etc.). |
| Extensions | Metadata such as key usage (digitalSignature, keyEncipherment) and Subject Alternative Name (SAN). |
| Signature Value | The digital signature generated by the issuing CA using its private key. |
During authentication:
- The ECU sends its certificate to the client.
- The client verifies it against the trusted CA’s root certificate.
- The client then sends its own certificate and signature.
- The ECU verifies it using the same process.
This mutual verification ensures trust and integrity in the communication.
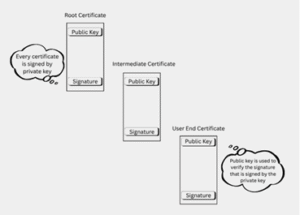
The verification process follows a chain of trust, usually consisting of three layers:
- Root Certificate Authority (Root CA):
The ultimate source of trust, self-signed and highly protected. - Intermediate Certificate Authority (Intermediate CA):
Acts as a bridge, issuing certificates to lower entities while protecting the Root CA. - End-User Certificate:
The certificate used by the ECU or tester during authentication.
Every certificate is signed using the issuer’s private key and verified using its public key — ensuring authenticity and integrity at each level.
(You can refer to the visual diagram showing the Root, Intermediate, and End-User Certificates to understand how trust flows from top to bottom.)
The Role of PKI in APCE
The Public Key Infrastructure (PKI) acts as the backbone of APCE. It defines how keys and certificates are generated, distributed, and validated.
In a PKI-based system:
- Each ECU and diagnostic tester holds a digital certificate issued by a Certificate Authority (CA).
- The CA serves as a trusted third party, ensuring that only authorized entities are recognized.
- Certificates can be revoked or renewed, allowing secure lifecycle management across the vehicle’s life.
This structure makes APCE ideal for large-scale automotive systems where many ECUs, tools, and backend servers interact dynamically.
Algorithms Used in APCE
APCE relies on cryptographic algorithms to perform key exchanges, digital signatures, and data integrity checks. The choice of algorithms determines the strength and performance of authentication.
Here are the common categories used:
- Asymmetric Encryption Algorithms
- Used for key exchange and signature verification.
- Examples: RSA, Elliptic Curve Cryptography (ECC)
- Hash Functions
- Used for challenge generation and integrity checks.
- Examples: SHA-256, SHA-512
- Digital Signature Algorithms
- Used to prove the authenticity of a message or entity.
- Examples: RSA Signature, ECDSA (Elliptic Curve Digital Signature Algorithm)
Why Elliptic Curve Cryptography (ECC) and ECDSA?
Elliptic Curve Cryptography (ECC) has become the preferred choice for automotive applications because it provides high security with smaller key sizes — an essential advantage for embedded ECUs with limited memory and processing power.
For instance:
- A 256-bit ECC key offers similar security to a 3072-bit RSA key
- This means faster computations, lower bandwidth, and reduced storage — all without compromising security
Within ECC, the ECDSA (Elliptic Curve Digital Signature Algorithm) is the algorithm most commonly used for digital signatures in APCE.
How ECDSA Works in Authentication
Let’s look at the ECDSA concept in simple terms:
- Key Generation:
Each party generates a private key (kept secret) and a public key (shared in its certificate). - Signing:
When the ECU or tester wants to prove its identity, it creates a digital signature over a message (like a challenge) using its private key. - Verification:
The other party uses the sender’s public key to verify the signature.
If the verification passes, it confirms that:- The message truly came from the claimed sender.
- The message was not tampered with during transmission.
This mechanism ensures both authentication and integrity — two critical pillars of secure in-vehicle communication.
Putting It All Together: Secure Vehicle Communication
With APCE and ECDSA, UDS 0x29 enables a powerful trust framework for modern automotive systems.
Each ECU can now authenticate itself using cryptographic proofs instead of relying on static secrets.
The diagnostic tester can confidently establish a secure session knowing the ECU’s identity is verified by a trusted authority.
As vehicles become more software-defined and connected, such mechanisms will form the foundation of automotive cybersecurity, ensuring every communication is both authentic and protected.
Conclusion
Authentication is no longer optional in the connected vehicle era — it’s a necessity.
While ACR provided a functional start, the shift toward APCE reflects the industry’s demand for scalable, certificate-based trust anchored in public key cryptography.
And with algorithms like ECDSA, we now have a method that balances security, efficiency, and performance — making it perfectly suited for the resource-constrained yet safety-critical world of automotive electronics.
The Authentication Service (UDS 0x29) is more than just another diagnostic service — it’s a critical shield that keeps vehicles secure, communications authentic, and the future of mobility trustworthy.

 WhatsApp us
WhatsApp us